LPI Linux Certification in a Nutshell (58 page)
Read LPI Linux Certification in a Nutshell Online
Authors: Adam Haeder; Stephen Addison Schneiter; Bruno Gomes Pessanha; James Stanger
Tags: #Reference:Computers

Fundamentals
(Topic 109.1)
Although it is not necessary for you to be a networking expert
to pass the LPIC Level 1 Exams, you must be familiar with networking,
network-related vocabulary, and basic Linux networking configuration. This
chapter introduces fundamental networking and troubleshooting concepts
specifically included in the exams. However, it is not a complete
introductory treatment, and you are encouraged to review additional material
for more depth. This chapter covers this Objective:
- Objective 1: Fundamentals of Internet
Protocols Candidates should demonstrate a proper understanding of
network fundamentals. This Objective includes the understanding of IP
addresses, network masks, and what they mean (i.e., determine a
network and broadcast address for a host based on its subnet mask in
dotted quad
or abbreviated
notation, or determine the network address, broadcast address, and
netmask when given an IP address and number of bits). It also covers
the understanding of the network classes and classless
subnets (CIDR) and the reserved addresses for private
network use. IPv6 is also discussed, along with how this addresses
some of the limitations of IPv4. It includes the understanding of the
function and application of a default route. It also includes the
understanding of basic Internet protocols (IP, ICMP, TCP, UDP) and the
more common TCP and UDP ports (20, 21, 23, 25, 53, 80, 110, 119, 139,
143, 161). Weight: 4.
The TCP/IP suite of protocols was adopted as a military
standard in 1983 and has since become the world standard for network
communications on the Internet and on many LANs, replacing proprietary
protocols in many cases. This section covers TCP/IP basics cited by the
LPI Objectives.
For several years IPv4 has been the standard method for
assigning a unique address that identifies the host on the network and
the Internet. The 32-bit IP address, also referred to as a
dotted quad
, is composed of four 8-bit fields
divided by a period. These fields identify first the network and then
the host for a device on the network. IPv4 provides 4.29 billion
addresses.
The IP address 192.168.1.150 and the binary equivalent would
be:
11000000 10101000 00000001 10010110
IPv4 addresses are categorized into classes to provide structure.
There are five classifications of networks defined by IP addresses.
Table 19-1
identifies the address
ranges for the classes that are primarily used.
Table 19-1. IPv4 address ranges by class
Address class | IP address range |
|---|---|
Class A | 0.0.0.0 to |
Class B | 128.0.0.0 to |
Class C | 192.0.0.0 to |
Class D | 224.0.0.0 to |
Class E | 240.0.0.0 to |
Every device on a network or connected to the Internet needs a
unique IP address, including printers and fax machines; consequently,
the supply of available IP addresses will run out eventually. There have
been many technologies developed to reduce the exhaustion of available
IP addresses, including network address translation (NAT), Classless
Inter-Domain Routing (CIDR), and IPv6.
One of the early attempts of handling the exhaustion of
IP addresses was the implementation of private IP addresses. Private
IP addresses are not globally assigned, which means that different
organizations may use the same private IP addresses. Private IP
addresses are not routable, and therefore they are not accessible
across the Internet. Organizations using private IP address internally
for network connectivity use a process called network address
translation (NAT) gateway or a proxy server to provide connectivity to
the Internet. Each IP address class has a range of IP addresses that
are reserved as private addresses.
Table 19-2
lists the ranges for
private IP addresses.
Table 19-2. IPv4 private network address ranges
Class | Private IP address |
|---|---|
Class A | 10.0.0.0 to |
Class B | 172.16.0.0 to |
Class C | 192.168.0.0. to |
In the 1990s it became apparent that the exhaustion of
the IPv4 addresses would be reached in a few years with the
ever-growing expansion of Internet technology. The move was made away
from assigning IP addresses based on classes to a method that uses
ranges of address. IPv4 addresses are now specified using the CIDR
notation that specifies subnet masks. The CIDR notation uses the
formataddress/prefix.
Theprefixdesignates the number
of bits that will be used by the subnet mask. Let’s say we have a
range of IP addresses consisting of 206.24.94.105 and a subnet mask of
255.255.255.0. We would note this address using CIDR as:
206.24.94.105/24
Using the CIDR notation allows for custom subnet masks to be
created without tying them to the limitations of classes.
The Internet Engineer Task Force (IETF) defined IPv6 in
1995. While IPv4 still has the majority of addressing, all network
operating systems and hardware device manufacturers support IPv6. IPv6
increases the size of IP addresses from 32 bits to 128 bits, or 16
octets. This increases the possible number of available addresses to a
maximum of 2
128
, or
3.42×10
38
, unique addresses. With the
large number of available IPv6 addresses, it is not necessary to
implement addressing conservation methods such as NAT and CIDR. This
will help reduce the administration overhead of managing
addresses.
The IPv6 address is composed of hexadecimal digits representing
4-bit sections separated by a colon. The addresses are represented by
the formatxxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx:xxxx.
An example of the preferred format for IPv6 addresses would look like
the following:
2130:0000:0000:0000:0003:0040:150c:235b
IPv6 may be abbreviated by removing the leading zeros from the
address, so if applied to the previous example, the address could
appear as follows:
2130:0:0:0:3:40:150c:235b
Another shorthand version of the IPv6 address uses double-colon
notation, wherein address sections that consist of a series of zeros
may be replaced with a double colon. In the instance of the IPv6
address 2130:0000:0000:0000:0003:0040:150c:235b, it could be shortened
to:
2130::3:40:150c:235b
IPv6 address several disadvantages of IPv4 addressing,
including:
- Limited addresses
As mentioned previously, IPv4 has only about
10
9
available addresses, and this
supply is expected to be exhausted in the near future. IPv6 has
a much larger addressing capability with
10
38
addresses.- Security
IPsec was designed to be integrated into IPv6 addressing
and is mandated to be used with the protocol, whereas IPv4
treats it as an optional function. Encryption processes are also
mandated to be included into IPv6 addressing.- Configuration
IPv6 devices will autoconfigure themselves when connected
to an IPv6-routed network. This process is a cleaner version of
the IPv4 DHCP process discussed later in this chapter. The
autoconfiguration functionality also improves addressing
assignments of mobile devices because these devices are assigned
to a “home” address where it remains always reachable. When the
mobile device is at home, it connects using the home address.
When the mobile device is not at home, a home agent, typically a
router, will relay messages between the mobile device and the
nodes it is communicating with.- Performance
IPv6 headers have been modified to fixed widths to work
with high-speed routers, increasing speed and performance when
moving data packets across Internet backbones.
On the Exam
Prepare to discuss the difference between public and private
IP addresses on the Internet. Also be able to discuss the major
differences between IPv4 and IPv6 addressing.
The early specification of the IP recognized that it would
be necessary to divide one’s given allotment of IP addresses into
manageable subnetworks. Such division allows for distributed management,
added security (fewer hosts can potentially snoop network traffic), and
the use of multiple networking technologies (Ethernet, Token Ring, ATM,
etc.). IP also enables convenient partitioning of the physical portions
of a network across physical and geographical boundaries. To provide the
capability to locally define networks, IP addresses are considered as
having two distinct parts: the part that specifies a
subnet
and the one that specifies a
network interface. (Remember that IP addresses are
assigned to network interfaces, not host computers, which can have
multiple interfaces. For this discussion, however, we assume a
one-to-one relationship between hosts and interfaces.) The boundary
between the network and host portions of an IP address is delineated by
a
subnet mask
, required by the TCP/IP configuration
of any network interface. Like the IP address, the subnet mask is simply
a 32-bit number specified in four 8-bit segments using
dotted
quad
decimal notation. The familiar class A, B, and C
networks have these subnet masks:
- Class A: 255.0.0.0 (binary
11111111.00000000.00000000.00000000) 8-bit network address and 24-bit host address
- Class B: 255.255.0.0 (binary
11111111.11111111.00000000.00000000) 16-bit network address and 16-bit host address
- Class C: 255.255.255.0 (binary
11111111.11111111.11111111.00000000) 24-bit network address and 8-bit host address
When logically AND’d with an IP address, the bits set to0in the subnet mask obscure the host portion
of the address. The remaining bits represent the network address. For
example, a host on a class C network might have an IP address of
192.168.1.127. Applying the class C subnet mask 255.255.255.0, the
network address of the subnet would be 192.168.1.0, and the host address
would be 127, as depicted in
Figure 19-1
.
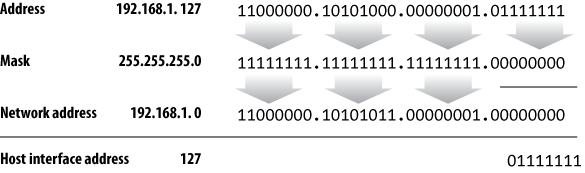
Figure 19-1. Host interface address calculation
Although it is typical to use the predefined classes (A, B, and
C), the boundary can be moved left or right in the IP address, allowing
for fewer or more subnets, respectively. For example, if a single
additional bit were added to the class C subnet mask, its IP address
would be:
- 255.255.255.128 (binary
11111111.11111111.11111111.10000000) 25-bit network address and 7-bit host address
With such a subnet defined on an existing class C network such as
192.168.1.0, the 256-bit range is split into two subnets, each with 7
host bits. The first of the two subnets begins at 192.168.1.0 (the
subnet address) and continues through 192.168.1.127 (the subnet
broadcast address). The second subnet runs from 192.168.1.128 through
192.168.1.255. Each of the two subnets can accommodate 126 hosts. To
extend this example, consider two additional bits:
- 255.255.255.192 (binary
11111111.11111111.11111111.11000000) 26-bit network address and 6-bit host address
When applied to a class C network, four subnets are created, each
with 6 host bits. Just as before, the first subnet begins at 192.168.1.0
but continues only through 192.168.1.63. The next subnet runs from
192.168.1.64 through 192.168.1.127, and so on. Each of the four subnets
can accommodate 62 hosts.
Table 19-3
shows more detail on class C subnets, considering only the host portion
of the address.
Table 19-3. Class C IP subnet detail
Subnet mask | Number of subnets | Network address | Broadcast address | Minimum IP address | Maximum IP address | Number of hosts | Total hosts |
|---|---|---|---|---|---|---|---|
128 | 2 | 0 | 127 | 1 | 126 | 126 | |
| | | 128 | 255 | 129 | 254 | 126 | 252 |
192 | 4 | 0 | 63 | 1 | 62 | 62 | |
| | | 64 | 127 | 65 | 126 | 62 | |
| | | 128 | 191 | 129 | 190 | 62 | |
| | | 192 | 255 | 193 | 254 | 62 | 248 |
224 | 8 | 0 | 31 | 1 | 30 | 30 | |
| | | 32 | 63 | 33 | 62 | 30 | |
| | | 64 | 95 | 65 | 94 | 30 | |
| | | 96 | 127 | 97 | 126 | 30 | |
| | | 128 | 159 | 129 | 158 | 30 | |
| | | 160 | 191 | 161 | 190 | 30 | |
| | | 192 | 223 | 193 | 222 | 30 | |
| | | 224 | 255 | 225 | 254 | 30 | 240 |
On the Exam
Be prepared to define network and host addresses when provided
an IP address and a subnet mask. Practice with a few subnet sizes
within at least one classification (A, B, or C). Also, because the use
of decimal notation can cloud human interpretation of IP addresses and
masks, be ready to do binary-to-decimal conversion on address
numbers.
As you can see, as the number of subnets increases, the total
number of hosts that can be deployed within the original class C address
range reduces. This is due to the loss of both broadcast addresses and
network addresses to the additional subnets.