Reverse Deception: Organized Cyber Threat Counter-Exploitation (69 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Throughout this book we have discussed many techniques and approaches for identifying the threat on your enterprise and how to lure them into systems of your choosing. These systems are the terrain you’re choosing to engage the threat on. Your entire enterprise can be looked at as your battleground and the locations you choose to engage are your terrain. Choosing the battle terrain is the single most important part in traditional combat. Evaluating and understanding your network (the battle terrain) is essential, as this will afford you the opportunity to limit the number of ingress (entry) and egress (exit) routes to and from your network. These are the points where you can concentrate your defenses against persistent threats. This will provide you a battlefield advantage and may stem the tide of information flowing out of your network. The key is to make your adversaries work harder for access to your network and the information it contains. Increase the cost per byte for your adversaries, and they may decide to pass you by.
Just sit back for a few more hours and keep reading. By the end of this chapter, you’ll know you are not so powerless. We’ll look at the tools and tactics you can use—the arrows in your quiver of tools, so to speak. We are going to discuss not only the tools (remaining vendor-agnostic) and where to best place them, but also some of the weaknesses of current solutions, such as host- and network-based systems.
You will also learn there are no silver bullets. No single company, product, or service can be an all-in-one solution. Traditional solutions have not been working as we all hoped. A decade ago, the threat was different, so security solutions were developed to address those vectors. Now the threats and their tools and techniques have evolved, and traditional security technologies have not been able to keep up, although they have been trying and continue to serve a purpose.

Detection Technologies
There are so many vendors that sell host-based and network-based security products that it is hard to tell which one is better than the other. Not every product or service is best for your environment, no matter what any vendor says. Sometimes a combination of a specific set of tools is all you need.
The larger your enterprise, the more tools you need due to the volume of data crossing your enterprise. A small firm of less than 100 users may need only one host-based solution and a few network-based security solutions. A network of more than 100,000 users could require a handful of host-based products (not all on the same machine) and several different types of network security solutions. An enterprise of a million or more users/subscribers would demand an array of host- and network-based solutions, as well as more complex information security protocols.
Hundreds of security products provide detection of malicious network activity. These technologies typically come in two flavors: host- or network-based security systems. Today, most solutions use a combination of signature, blacklist, behavior, and anomaly-based detection techniques. These tools all have their pros and cons.
Tables 8-1
and
8-2
list some detection tools in alphabetical order (to not show any favoritism). These are the most prominent tools in the industry as of the second quarter of 2011. Most of these tools are complementary between the network and enterprise, and you will find that many have similar functionality at their own levels.

Table 8-1
Host-Based Detection Tools
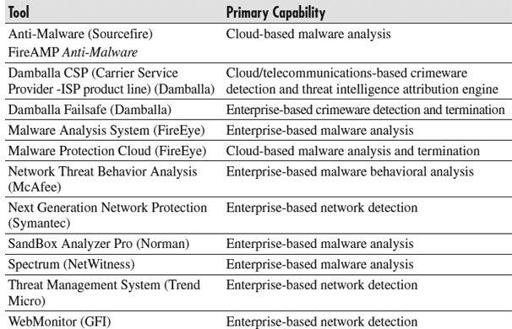
Table 8-2
Network-Based Detection Tools

Host-Based Tools
In their simplest form, host-based security controls are the measures (applications) put in place to monitor the state of an individual host. They will monitor a system to determine if a malicious file is present, an application attempts to make changes to certain files, or any number of activities occur that may fall under the malicious category. More advanced implementations of host-based security controls include the use of an advanced application whitelist, which, in essence, tells the computer which applications it is allowed to run.
If planned and deployed properly, these tools can be used to take action against persistent threats. One major consideration is that host-based technologies are not the magical cure to what ails your network. They are just the first step in increasing your overall security posture, leaving you in a better position when facing persistent threats.
We’ll cover the following categories of tools that will help improve your host-based security posture:
Antivirus
Digital forensics
Security management
Antivirus Tools
Antivirus solutions have been around for well over a decade, and they have needed to evolve at a rapid pace in order to keep up with the ever-changing threat landscape. However, when it boils down to it, generally these solutions are easier to circumvent than network-based security systems. Although these solutions do catch and prevent a significant number of malicious activities from executing, when it comes to an advanced or organized threat, these systems will be circumvented.
Things to Think About
Here are some tips on how you could increase your antivirus system as a force multiplier:
What kind of data do you need from your antivirus clients?
You need to know that it is enabled, it is detecting, and it is updated. You also need to know what is being detected and check the activity logs.
What is one way to identify when your antivirus may be disabled?
When it stops its heartbeat. Most people don’t realize there are options and logs for this information.