Oracle Essentials Oracle Database 11g (28 page)
Read Oracle Essentials Oracle Database 11g Online
Authors: Rick Greenwald

This section provided only a very brief overview of standard backup and recovery.
For more information on providing high availability, refer to Chapter 11.
Oracle Secure Backup
Oracle began bundling its own Secure Backup solution with Oracle Database 10
g
.
Called Oracle Secure Backup Express (XE), it replaced Legato’s Single Server Version (LSSV) tape storage management. Since Enterprise Manager 10
g
Release 2, Secure Backup is integrated into the Enterprise Manager interface. Secure Backup XE
leverages RMAN’s reading the database block layout directly and provides tape data protection for one server attached to one tape drive. Where an enterprise solution is needed, Oracle offers an optional Secure Backup version that can support multiple drives for any number of servers.
Backup and Recovery
|
135
Oracle Secure Backup provides support for more than 200 different kinds of tape drives. Secure Backup also provides Netwrok Data Management Protocol (NDMP) support for network attached storage (NAS), Virtual Tape Library (VTL) support, policy-based management, storage classification, dynamic drive sharing, certificate-based authentication, and the ability to create encrypted backups.
Of course, there remain a wide variety of alternative solutions available providing Oracle backup solutions. Oracle continues to maintain the Oracle Backup Solutions Program (BSP) such that partners can certify their products to perform backup and recovery for tape storage devices using RMAN. A current list of these solutions is posted on the Oracle Technology Network web site.
Information Lifecycle Management
Information Lifecycle Management (ILM) provides a means to define classes of data, create storage tiers for the data classes, create data access and data movement policies, and implement data compliance policies. ILM is most frequently used to move data among various devices that are most appropriate for hosting that data, such as different classifications of disk. The reason for doing this is that most administrators would like to have their most frequently accessed data on the fastest but most expensive disk, and the least frequently accessed data on the on the slowest but cheapest disk.
Oracle first began supporting ILM in 2006 for database releases dating back to Oracle9
i
and introduced a tool, the ILM Assistant, that can be downloaded from the Oracle Technology Network. In addition to the ILM Assistant, youwill need to have Oracle Application Express (formerly HTML DB) installed in the database where the data is managed.
The ILM Assistant presents a graphical user interface used in creating lifecycle definitions and policies for database tables. It can advise when it is time to move, archive, or delete data and also illustrate cost savings and storage required. The ILM Assistant can also guide you in creating partitioning to match your ILM needs. Once you have defined a strategy, it generates the scripts for moving the data.
The first time youstart the ILM Assistant, youshould select the Lifecycle Setup tab.
On this tab youdefine logical storage tiers, create lifecycle definitions, and select the tables to be managed (see
Figure 5-4).
The ILM Assistant can then provide advice on data placement. Optionally, you can also view partition simulation, a lifecycle summary, and storage costs, and can define policy notes.
In subsequent restarts of the ILM Assistant, you will see a Lifecycle Events Calendar that will display a list of all outstanding events. The calendar, and also the events and history of event scans, might be viewed subsequently by selecting the Lifecycle Management tab.
136
|
Chapter 5: Managing Oracle
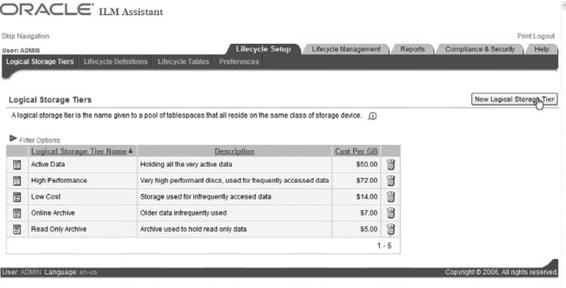
Figure 5-4. Oracle Information Lifecycle Management Assistant
A number of reports are provided under the Reports tab, including multitier storage costs by lifecycle or table, logical storage tier summary, partitions by table or storage tier, lifecycle retention summary, and data protection summary. Under the Compliance and Security tab, you can view the status of virtual private database (VPD) policies and when digital signatures were generated; create digitally signed result sets for tracking immutability; view a summary of privacy and security definitions, policies, views, and access privileges; manage and view fine-grained audit (FGA) policies; and view and provide policy notes.
Working with Oracle Support
Regardless of the extent of your training, there are bound to be some issues that you can’t resolve without help from Oracle Corporation. Part of the job of the DBA is to help resolve any issues with the Oracle database. Oracle offers several levels of support including basic product support, advanced support, and incident support. Each of these support options costs extra, but regardless of your support level, you can get the most from Oracle by understanding how to best work with them.
Resolving problems with the assistance of Oracle Worldwide Customer Support Services can initially be frustrating to novice DBAs and others who may report problems. Oracle responds to database problems reported as Service Requests (SRs), sometimes referred to by their old name as Technical Assistance Requests (TARs).
The response is based on the priority or severity level at which those problems are reported. If the problem is impacting your ability to complete a project or do business, the problem should be reported as “priority level 2” in order to assure a timely response. If the problem is initially assigned a lower level and the response hasn’t been adequate, you should escalate the problem-resolution priority.
Working with Oracle Support
|
137
If business is halted because of the problem, the priority level assigned should be
“priority level 1.” However, if a problem is reported at level 1, the caller must be available for a callback (even if after hours). Otherwise, Oracle will assume that the problem wasn’t as severe as initially reported and may lower the priority level for resolution.
Reporting Problems
Youcan report problems via phone, email, or the web browser-based MetaLink interface. MetaLink support, included with basic product support, has grown extremely popular as answers to similar problems can be rapidly found by you directly, which may result in eliminating time required for a physical response. MetaLink provides proactive notifications, customized home pages, technical libraries and forums, product lifecycle information, a bug database, and the ability to log SRs.
When contacting technical support, you will need your Customer Support Identification (CSI) number. Oracle Sales Consultants can also provide advice regarding how to report problems. Additionally, Oracle Worldwide Customer Support Services offers training for DBAs regarding effective use of Support services.
As we noted earlier, Oracle Database 11
g
provides a Support Workbench in Enterprise Manager that youcan use to report problems. This release also offers a SQL
Test Case Builder that can help Oracle Support re-create the problem and resolve it sooner. Youtypically would first see problems as critical error alerts on the Enterprise Manager Database home page, then would view problem details, gather additional information, create a SR, package and upload the diagnostic data to Oracle Support, then track the SR and close it when resolved.
Automated Patching
Oracle Support issues MetaLink Notes whenever software bugs or vulnerabilities are discovered and issues appropriate patches. Automated patching and notification provided since Oracle Database 10
g
can reduce the time delay between Oracle’s discovery of such problems and your reaction to them. Alerts can now be issued to your Enterprise Manager console alerting you to the newly discovered bugs or vulnerabilities. Through the Enterprise Configuration Management capabilities in Enterprise Manager, you’ll see a link to the patch and the target where the patch should be applied.
In RAC and grid environments, “rolling” patch updates can be applied across your nodes without taking the cluster or grid down. (We described the process of applying rolling patch updates in
Chapter 3.)
Further, you can roll back a patch (e.g., uninstall it) on an instance if you observe unusual behavior and want to remove the patch.
138
|
Chapter 5: Managing Oracle
Chapter 6
CHAPTER 6
Oracle Security, Auditing, and
Compliance6
The primary purpose of Oracle database software is to manage the valuable data that lies at the core of virtually every operation in your organization. Part of the value of that data is that the data is
yours
—the data that can be used to give your company unique advantages. For this reason, you need to protect your data from others who should not have access to it. This protection is the subject of this chapter. Here we focus on three different aspects of the overall task of protecting your data:
•
Security
covers the tools that youuse to allow access only to those people you designate.
•
Auditing
allows you to discover who did what with your data. Auditing is the process of creating a history of access that can be used to understand database operations as well as spot access violations and attempts. When youare configuring Oracle Database 11
g
, youwill be asked if youwant to keep the default security settings. If you do, auditing will be enabled and a new default password profile option will be in place. A number of other database initialization parameters will be reset at this time.
•
Compliance
is the ability to prove that your data is secure and reliable—a proof that is now legally required in many cases. Although compliance may strike many technical folks as overkill, the simple fact is that a lack of compliance alone may result in significant penalties to your company. Compliance is thus a topic of great interest to management.
Security
One of the most important aspects of managing the Oracle database effectively in a multiuser environment is the creation of a security scheme to control access to and modification of the database. In an Oracle database yougrant security clearance to individual users or database roles, as we describe in the following sections.
139
Security management is typically performed at three different levels:
• Database level
• Operating system level
• Network level
At the operating system level, DBAs should have the ability to create and delete files related to the database, whereas typical database users do not need these privileges.
Oracle includes operating-system-specific security information as part of its standard documentation set. In many large organizations, DBAs or database security administrators work closely with computer system administrators to coordinate security specifications and practices.
Database security specifications control user database access and place limits on user capabilities through the use of username/password pairs. Such specifications may limit the allocation of resources (disk and CPU) to users and mandate the auditing of users. Database security at the database level also provides control of the access to and use of specific schema objects in the database.
Usernames, Privileges, Groups, and Roles
The DBA or database security administrator creates
usernames
that can be used to connect to the database. Two user accounts are automatically created as part of the installation process and are assigned the DBA role: SYS and SYSTEM. (The DBA role is described in a later section.)
Each database username has a password associated with it that prevents unauthorized access. A new or changed password should:
• Contain at least eight characters
• Contain at least one number and one character
• Not be the username reversed
• Differ from the username or use name with 1 through 100 appended
• Not match any word on an internal list of simple words
• Differ from the previous password (if there is one) by at least three characters Oracle can check for these characteristics each time a password is created or modified as part of enforced security policies.
Once a user has successfully logged into the database, that user’s access is restricted based on
privileges
, which are the rights to execute certain SQL commands. Some privileges may be granted systemwide (such as the ability to delete rows anywhere in the database), while others may apply only to a specific schema object in the database (such as the ability to delete rows in a specific table).
140
|
Chapter 6: Oracle Security, Auditing, and Compliance
Roles
are named groups of privileges and may be created, altered, or dropped. In most implementations, the DBA or security administrator creates usernames for users and assigns roles to specific users, thereby granting them a set of privileges.