Reverse Deception: Organized Cyber Threat Counter-Exploitation (124 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

The following shows what the control panel for a SpyEye CnC server looks like upon connection.
Once you have used the preceding script to inject your own user account, you are able to log in to the CnC server covertly without the knowledge of the criminals (unless they check their server or connection logs often). There is always a chance of getting caught by the criminals. In our practical usage of these techniques, we have found that if we simply log in and modify a criminal’s infrastructure—by banning, deleting, or altering settings in a way that will cause some level of damage to their campaign—they often back off from the CnC server. This may be because they fear that their true identities, or ties to their real-life identities through private e-mail or names, could lead to attribution to that specific crimeware support infrastructure. Again, this is not always the case, but it has been a very effective tool when attempting to manipulate a remote adversary without tying up any personnel beyond a few smart network ninjas for a few hours.
Note that the legality of these techniques depends on which country you live in. This is probably illegal, and if you get caught, you will be in trouble (although we never worry about a specific criminal trying to file charges against us for infiltrating their infrastructure). You may run into a law enforcement agency that is actively working against that criminal, and you have just tainted their evidence (bad mojo on the receiving end). This generally does not end up well for the security professional with the good intentions.
In almost every country around the world, hacking is illegal. There are a handful of countries that allow it, or look the other way as long as you don’t hack anything in your own country. These include Brazil, Russia, China, Iran, and Holland (where Wi-Fi hacking is legal). So again, if you perform actions like these, you can open yourself up to legal turmoil. Many highly skilled professionals have been caught performing these proactive defensive actions against advanced or organized cyber threats over the years, and they have lost their jobs and permanently marred their careers. Please be aware of the fact that every action has a reaction, and some have very serious consequences if you step on the wrong toes.
Now back to our analysis of an exploited criminal. Upon first logging into the SpyEye control panel shown earlier, we dig into the following credit card information page.

We see that this criminal has not collected any of his victims’ credit card information. That’s interesting. So it appears that this criminal campaign does not have any focus on financial information. What is this criminal campaign after? This threat was monitored for over six months, so we were able to come back again and again to see the increase and decrease of victims and what information was stolen. Now we check the Bank of America credit card grabber, and we see the criminal has not used any of the credit card grabbing tools.
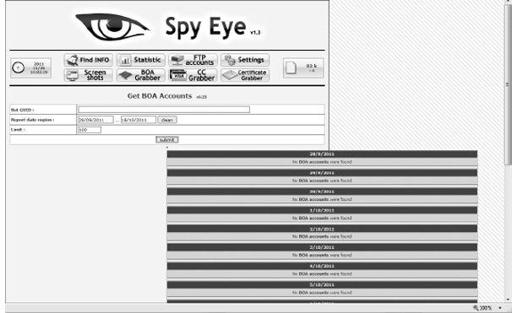
This observable information tells us that our hypothesis is correct: this criminal is not interested in financial information, or this criminal did not have the funds to purchase the credit card grabber add-on for the SpyEye malware builder, which generally goes for over $1,000. As you can also see, there are several other options and features available to our counterintelligence team to learn about this specific threat’s campaign. You may wonder why we look to the financial information first. The reason is very simple: the faster security professionals can discern whether a crime was financially motivated, the faster they can react. It has the following benefits:
You can alert law enforcement of the victim’s country so the victims can be properly notified in a timely manner.
This can serve as one of many indicators of an opportunistic or a targeted threat.
This allows you to see how long the criminal has been collecting financial information.
You can better understand what types of financial institutions the criminal has access to.
Now let’s move on to the actual statistics page.
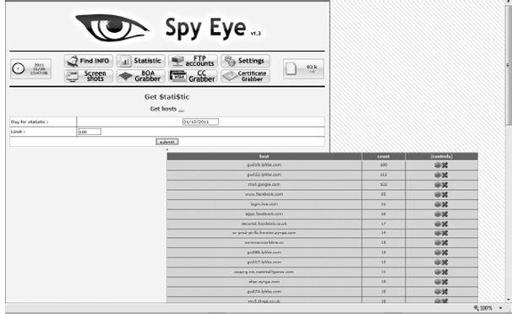
Here is where we get to the meat of this threat’s activity. Based on the activity of the statistics page, we can see that numerous accounts were stolen, ranging from social networking site accounts to personal and professional online accounts. We can see that this criminal is seeking additional access to exploitable accounts that can be sold in bulk on underground forums all over the world (those mentioned in
Chapter 3
and others springing up every day).
Scrolling down the statistics page, we see more information.
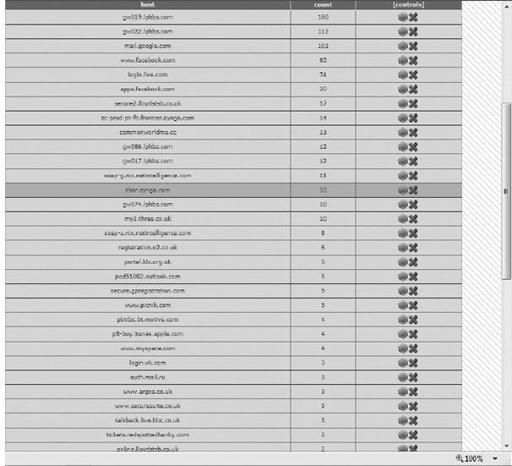
All of these domains have accounts (username and password combinations, along with any data accessible with those credentials) associated with them that were stolen from various victims. In the control panel on the top-right side, you can see the number 83k, which is the number of bot victims this criminal had at the time of our latest analysis of this campaign.
The analysis team who worked on this criminal’s dossier has thousands of accounts we simply do not have the time or space to cover in the book. Just know there were originally 254,000 victims on this threat’s CnC server before ep0xe1 banned and deleted access to over 150,000 of the threat’s bots. He removed victims of countless Fortune 500 firms in order to minimize this threat’s ability to sell off specific accounts on the black market to criminals who are interested in more than simple financial theft or continued infection campaigns.