Reverse Deception: Organized Cyber Threat Counter-Exploitation (125 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

In the following screen, we can see that this same criminal was also focused on collecting e-mail certificates and e-mail account information from each victim.
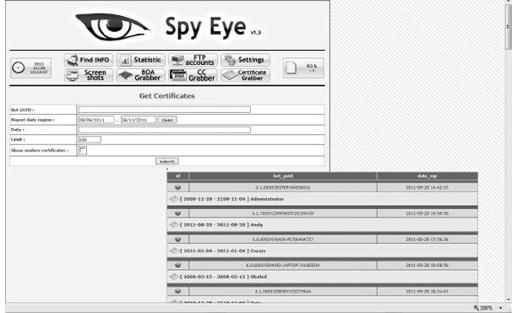
This information is important, as it can be used in targeted attacks such as spear phishing, whaling, or other e-mail-based attacks, where a victim’s account and reputation or identity can be exploited through the trust others have in this individual. For the safety of each victim, we will not disclose the information about the actual certificates, as they are directly attributable to a specific individual or international organization. As you can see in the screenshot, there is a hefty list of more than 100,000 e-mail accounts and e-mail certificates collected by this threat that are possibly exposed and actively being sold on the black market. The final item we check is the information page of each specific SpyEye victim and the associated information the bots running on their systems are sending to the threat. Again, for the sake of the victims, we have analyzed and deleted from the criminal’s infrastructure well over 100,000 entries of victim data.
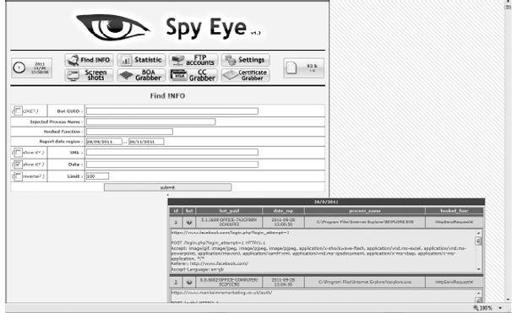
This page shows the following information:
SpyEye bot GUID
Unique to each victim
Timestamp
When the data was collected
Process
The process through which the bot is collecting information
Hooked function
Which function is being exploited to collect victim information. As you can see, there is a lot of unique information that can be gleaned from the functionality of the bot itself. Every victim has hundreds of entries, as the bot sends data back to the CnC server on a regular or timed period.
Practically every bot or remote Trojan collects and reports information similar to SpyEye. Although not all criminal control panels have as pretty a user interface as this one, the functionality is still there.
Since this initial attribution work was performed, SpyEye has begun to wane in popularity among criminals. Newer variants of Zeus—such as Ice-IX, Citadel, and Zeus version 3 (Gameover)—and thousands of other bot kits, crimeware builders, remote-access Trojans, and worms that report back victim information are being sold on the underground markets. Knowing there are proactive defensive tactics that go beyond your own enterprise and engage the threat directly is important. If you cannot allow this yourself, get law enforcement agencies involved, and they can help in shutting down the infrastructure.
The attribution outcome of this specific threat was that it was targeting large organizations and individuals who worked for big international firms and stealing their e-mail credentials. So this threat was ranked with a reputation score of 8 based on the observables list presented in
Chapter 3
.

Conclusion
This book has led you through many paths of analysis and operational techniques that can improve your security posture beyond the traditional antivirus, basic perimeter defenses, crimeware detection and mitigation, and security firms who deal with these issues on a daily basis. We have walked through different scenarios involving enemy engagement, exploring the tactics that allow your adversary to be successful, and discussed how these new skills can be useful when you face your enemy.
As you begin to conduct operations yourself, some will be successful and some will not meet the desired end. That is the nature of the beast. One key to success is to share the information about your attackers and the measures you took to fend them off with the rest of the security community, to the extent allowed. One person will not win the war, but the security community can win many battles together, propelling it to victory.
There are hundreds of security professionals who work in the same circles to be aware of the latest threats. Their tools and techniques can be countered or engaged in order to mitigate a threat. Between the resources in this book and the specific individuals named in this chapter, you are a member of an organization. No matter where in the world you are, subject matter experts are available to work with you in private or with law enforcement to engage, mitigate, or exploit threats and prevent further hemorrhaging of your infrastructure.
The overall goal of this book is to empower you and your organization to better handle advanced cyber threats in the future and increase the security posture of your organization from targeted or opportunistic cyber threats. We hope you walk away from this book feeling empowered and informed on some of the latest techniques from some of the professionals who do analysis and attribution as a way of life to better protect their organization, customers, and the global Internet. Advanced cyber threats emerge almost every day, and knowing which are specific to your organization or enterprise is much more important than the total volume of infections across your enterprise. We highly recommend that you contact one of the authors or professionals listed in this chapter to learn more about threats before they’re actually within or working against your organization.
Working in unison is the only way we can reverse the enemy’s deception, seeing that there is nothing we can do to stem the encroachment of organized or advanced cyber threats. It is your network and our infrastructure. Prepare yourself and attempt to take the fight to the enemy (focus). You will walk away from your office at the end of the day feeling much better, knowing you had a hand in identifying and attributing criminal campaigns back to a specific group or individual.
What’s next? Who knows? We continuously see evolutions and variants of criminal tools and tactics. We’re sure that after reading this book, some criminals will alter some of their techniques and attempt to counter the counterintelligence tactics conveyed here. To date, honeypots have been widely distributed only by a handful of private organizations and vendors. There are small groups within international governments, like the United States, United Kingdom, China, and the United Arab Emirates, who have a national-level based
honeygrid
(a massive network of connected honeynets), a term coined by one of the initial thought leaders and one of the Honeynet Projects within the US government, US Marine Corps Major Allen Harper (now retired).
Deception is a way of life for some and either a state of mind or practice that can also be used as a weapon. Just read up on your
Art of War
by Sun Tzu. Deception and the countering or reversing of one’s deception are some of the most important capabilities that should be applied to every defense-in-depth security model.
